Overview
Terraform Cloud is service managed by HashiCorp that simplify the state management improve operator confidence. Projected to scale and simplify the usage best practices in a very transparent form.
Step zero is log and create an free account in Terraform Cloud link here. After login you will be asked to create an Organization this will be the ground zero to start.
The first step into Terraform Cloud will be create an workspace. The definition of workspace for Terraform cloud is slit different from Terraform OSS but same principles apply however for Terraform Cloud workspaces are more isolated and can be mapped to Source Control.
Once we start to scale collaboration will be required. Be productive in a team will require:
- usage of source control repositories;
- code using more dynamic approaches
- usage of better descriptions in code and operations
- enforce corporate directives
Terraform Cloud is projected in a form that guide users to adopt this kind of practices in a very intuitive form.
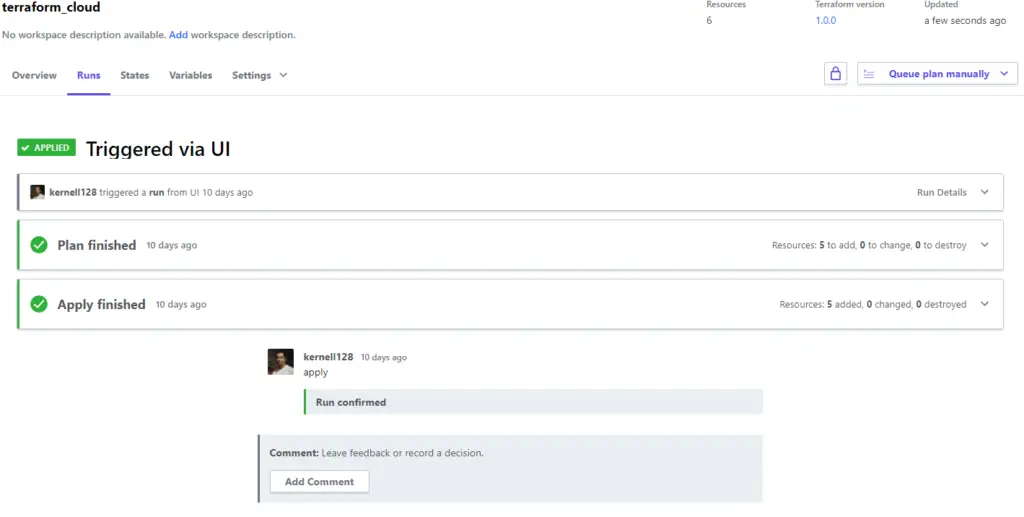
Once you deploy the corporate structure to work in the source control repo you can request/schedule plan/destroy/apply operations in Terraform Cloud adding the comments for each operations. Each operation will be added in history of workspaces.
Small Prototype
To demonstrate this in practice I choose use Microsoft Azure – you can use the free account. create the minimum structure to create an vNET. In git repo code will be able to be clone check how to configure the terraform.tfvars to define the proper authentication configuration.
For this prototype the VCS used is GitHub.com.
Repository: https://github.com/kernell128/terraform_cloud
git address: [email protected]:kernell128/terraform_cloud.git
OBS: Concept here was build an small prototype using network. In future new services can be added.
The first step after create or has an account is configure the credentials. Assuming that you have already installed AzureCli and have administrate access in Azure access the portal subscription link. Take note of SubscriptionID has the format: xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx .
run replacing with the proper subscription id:
az ad sp create-for-rbac –role=”Contributor” –scopes=”/subscriptions/xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx“
The output of this command will be five key value pairs.
{
“appId”: <<HASH>>,
“displayName”: <<HASH>>,
“name”: <<HASH>>,
“password”: <<HASH>>,
“tenant”: <<HASH>>
}
Take note of those values.
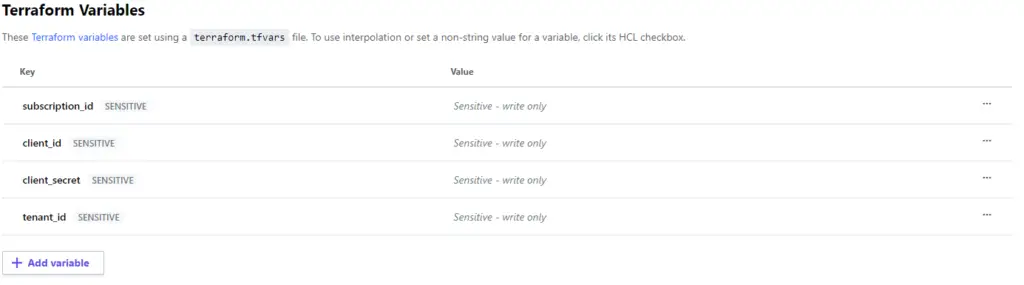
In Terraform Cloud settings you can define credentials under variables section in workspace.
Remember MARK as sensitive all of the following values once you save will not be displayed again.
Terraform Cloud require the following attributes:
- subscriptionID: no changes use the value from portal UI
- client_id is appId
- client_secret is password
- tenant is tenant_id
Terraform Cloud Variables
Terraform Cloud - Plan
Terraform Cloud - Apply